Ransomware: What can you do?
There’s little doubt that ransomware is a serious risk to businesses globally. The roll call of victims includes some of the biggest names in both international and local business: Colonial Pipeline, JBS Meats, Uniting Care, Channel 9 and Toll Holdings. In June 2021, the chief of the UK’s National Cyber Security Centre said ransomware was the key threat facing the UK.[1] It’s a risk that should be on every board’s risk register.
This post looks at what ransomware is, whether you should pay, and some recommendations on how to reduce the ransomware risk.
What is ransomware?
Ransomware is a type of malware that prevents you from accessing your computer (or the data that is stored on it). The computer itself may become locked, or the data on it might be stolen, deleted or encrypted. Some ransomware will also try to spread to other machines on the network, such as the Wannacry malware that dramatically impacted the UK hospital system in May 2017.
Usually you’re asked to contact the attacker via an anonymous email address or follow instructions on an anonymous web page, to make payment. The payment is invariably demanded in a cryptocurrency such as Bitcoin, in order to unlock your computer, or access your data.
Attackers may also threaten to publish data if payment is not made (a sort of reverse-ransomware threat).
Why is ransomware on the rise?
Reasons for the rise in ransomware include the development of the Ransomware as a Service (RaaS) model. This make a ransomware off-the-shelf toolkit available to ‘distributors’ for a one-off payment or a share of the profits. Avaddon is an example of this model.[2] Avaddon first appeared in March 2020, functioning as a ransomware-as-a-service operation, provding a portal for affiliates to generate and use copies of their crypto-locking malware. Every time a victim paid a ransom, the operator and affiliate shared the profits.
Like many operations, Avaddon also ran its own, dedicated data leak site, where non-paying victims could be named and shamed and extracts of data stolen from their infrastructure leaked to increase the pressure to pay a ransom.
There’s no reason why criminal organisations can’t borrow franchise and distribution network business models from the non-criminal world. As the RaaS model has become increasingly successful, with criminal groups securing significant ransom payments from large profitable businesses who cannot afford to lose their data to encryption or to suffer the down time while their services are offline, the market for ransomware has become increasingly “professional”.
To pay or not to pay?
In a recent research report, Forrester Research argued that paying ransomware should be viewed as a viable option and evaluated like any other business decision. However, this is counter to conventional wisdom.
However, the overwhelming advice from law enforcement and official cybersecurity bodies is not to pay the ransom. Law enforcement in particular do not encourage, endorse, nor condone the payment of ransom demands.
The Australia Cyber Security Centre (ACSC) strongly recommend that you do not pay. The ACSC advises that, if you do pay the ransom:
- there is no guarantee that you will get access to your data or computer;
- your computer will still be infected;
- you will be paying criminal groups; and
- you’re more likely to be targeted in the future.
The risk of a second attack seems to be supported by evidence. Boston-based Cybereason found 80% of organizations that previously paid ransom demands confirmed they were exposed to a second attack, according to a commissioned survey of 1,263 cybersecurity professionals in varying industries from the U.S., United Kingdom, Spain, Germany, France, United Arab Emirates and Singapore.[3]
In terms of getting your data back, it seems that ransomware attackers are pretty reliable. Sonos reports that 1% of organizations pay the ransom and never get their files back. Looking at country-specific statistics, India has the highest percentage of organizations that decide to pay the ransom (66%), while Spain has the lowest (only 4%).
Notwithstanding the law enforcement and security professional advice, for many businesses paying the ransom is the only way they will be able to get back to normal operations.
Is the tide turning?
There are increasing reports of ransomware operations closing the door. Ransomware-as-a-service operations and gangs come and go all the time. But lately, there’s some suggestion that the pressure on gangs and occasional disruption of their payment streams may have been driving more criminals to curtail their activities.
In April, for example, the Babuk operation announced it would stop attacks – although still offer its malware for sale to others – following fallout over its high-profile hit on the Metropolitan Police Department of Washington, D.C. Following its recent activities at Colonial Pipeline, Darkside has announced that it was suspending affiliate services. “The affiliate program is closed. Stay safe and good luTheck,” DarkSide claimed.
Avaddon, discussed earlier, has released a a free decryptor, amid speculation that is it closing down operations.[4]
As was seen in the Colonial Pipeline case, [6] where the Department of Justice announced it had recovered $2.3 million of the $4.4 million that Colonial Pipeline paid to DarkSide, FBI and other law enforcement agencies can interrupt the virtual currency payments that make the ransomware model work. This ability to interrupt the payment stream may have significant consequences for the business model of the ransomware purveyors and users.
Will ransomware drive greater regulation?
Since the ransomware attack on Colonial Pipeline in May, the U.S. Department of Homeland Security, through its Transportation Security Administration and CISA, has added cybersecurity requirements for the oil and gas industry.[5] In May 2021, President Biden also released an Executive Order which nudges the US federal government toward migrating to more secure cloud systems and establishes a “Cybersecurity Safety Review Board” with members from both the public and private sector.
In Australia on 21 June 2021, Labour introduced a private members’ bill to the House of Representatives which would launch a scheme requiring organisations to notify the Australian Cyber Security Centre (ACSC) if they are planning to make a ransomware payment.[7]
The bill would establish a mandatory reporting requirement for Commonwealth entities, state or territory agencies, and corporations (with an annual turnover of more than $10m) who are making a payment in response to a ransomware attack.
The purpose of the legislation is to ‘allow our signals intelligence and law enforcement agencies to collect actionable intelligence on where this money is going so they can track and target the responsible criminal groups.’ Information would also be used to inform Australian authorities and policymaking in the space.
Although not stated as an objective, the deterrent power of the mandatory notification of payments should not be ignored. Mandatory reporting of payments and the associated publicity will certainly become a factor in considering whether or not to pay a ransom. Many business may well re-think paying the ransomware if that must be reported and runs the risk of getting into the public domain.
What can you do?
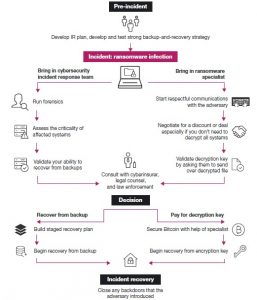
The best response to the rising ransomware threat is to make sure you and your organisation are prepared. Security leaders must understand and counter new ransomware challenges, strengthen defences across people, processes and technology and demonstrate why security is critical to the business strategy.
There are some steps you can take to reduce the likelihood and impact of a ransomware attack and to help with a quick recovery. The following advice is from the ACSC:
- Update your device and turn on automatic updates
- Turn on two-factor authentication
- Setup and perform regular backups, and stored them off-site on an unconnected network
- Implement access controls
- Turn on ransomware protection
- Prepare your Information Security Incident Response and identify what you will do in the case of a successful ransomware attack.
Organisations should also take measures to minimise the impact of data exfiltration. The UK NCSC’s guidance on Protecting bulk personal data and the Logging and protective monitoring guidance can help with this.
Ransomware attacks: Why and when it makes sense to pay the ransom | ZDNet
What about cyber insurance?
There has been an ongoing discussion about how insurers may play into ransom payments and even play a role in negotiations given it may keep costs down.
Cybersecurity insurance is one of the main anti-ransomware trends in today’s cyber world. In fact, 84% of organizations report having it. In times of security breaches, it can aid financially. However, only 64% of organizations have policies that cover ransomware incidents, meaning that the other 20% aren’t protected in such cases.
Of those organisation that have cybersecurity insurance, ransomware attacks were the cause of 41% of the claims filed over the first six months of 2020, according to a report published by Coalition, a cyber-insurance vendor that compiled the data based on findings from 25,000 small and medium-sized companies in the U.S. and Canada.[8] When organizations with anti-ransomware insurance are targeted by hackers and decide to pay the ransom, 94% of the time, it’s actually the cybersecurity insurance companies that cover the cost.
When considering cyber insurance, It is important to:
- Understand your cyber coverage and how it can protect you from ransomware;
- Are there any requirements on your organisation that must be met to trigger access to the insurance;
- How and when you might your insurer involved; and
- How to quantify costs to establish the insurance claim amount.
Ransomware attacks: Why and when it makes sense to pay the ransom | ZDNet
How can Privacy108 help?
Ransomware Training
Privacy108 are experts in security awareness training. Our instructors have been delivering security and privacy training for over 15 years.
Your people and their devices are at the front line of ransomware attacks. Ensuring they are properly trained and remain alert and vigilant is a vital part of your ransomware defence program.
Our team can assist with rolling out computer-based training, using existing collateral, or with the development and delivery of more targeted training, including practical lab based sessions, tailored for your own environment. To help arm your team to deal with ransomware, Privacy108 offer the following:
- Employee security awareness training, focusing on the human centric attacks;
- Lab exercises to train your front line and incident response teams;
- Ransomware exercises – both table top and ‘real’ to truly test your team’s readiness;
- Development of an Information Security Incident Response Plan;
- Creation of Ransomware Response Playbooks for your team.
Footnotes:
[1] NCSC CEO warns that ransomware is key cyber threat – NCSC.GOV.UK
[2] Avaddon Ransomware Operation Call It Quits, Releases Keys (databreachtoday.com)
[3] 80% of ransomware victims suffer repeat attacks, according to new report – CBS News
[4] Avaddon Ransomware Operation Call It Quits, Releases Keys (databreachtoday.com)
[5] DHS Unveils New Cybersecurity Requirements for Pipelines
[6] How Did FBI Recover Colonial Pipeline’s DarkSide Bitcoins?
[7] Labor introduces ransomware notification bill – InnovationAus
[8] Ransomware to blame for nearly half the cyber-insurance claims filed in early 2020 (cyberscoop.com)