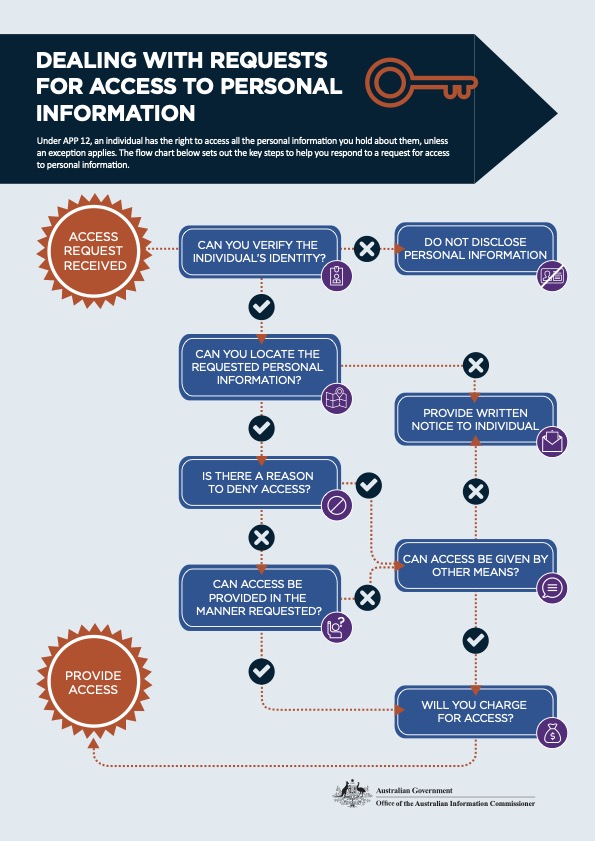
Responding to Access Requests: Practical Tips to Meet Your Privacy Obligations
Organisations covered by the Australian Privacy Act must provide access to the personal information the organisation holds about an individual, usually within 30 days. This isn’t always easy. In this blog post, we’ll outline some information how and when to respond to an individual’s access request.
Which Organisations Have to Respond to Access Requests in Australia?
As outlined above, Australian Privacy Principle 12 provides that organisations covered by the Australian Privacy Act must respond to access requests ‘within a reasonable time’. Most of the time, a reasonable time will mean within 30 calendar days (or less). So, organisations should have processes in place to swiftly respond to access requests.
However, it can be a good practice for organisations that aren’t covered by the Australian Privacy Act to accept and respond to access requests. Customers do now expect to be able to manage their privacy. So, organisations can gain a competitive advantage by increasing a customer’s privacy rights.
What Exceptions Exist for Access Requests?
Organisations do not need to respond to an access request if:
- The requester’s identity can’t be verified.
- You don’t ‘hold’ (or can’t find) the information requested.
- One (or more) of the grounds for refusal exist (see more below).
- You can’t provide access in the manner requested – or any other reasonable manner.
Download this chart: https://www.oaic.gov.au/__data/assets/pdf_file/0015/1068/flowchart-access.pdf
Grounds for Refusal
The OAIC lists the following grounds for refusal to provide access (in brief):
- Access would pose a serious threat to the life, health, or safety of an individual or the public.
- Another individual’s privacy would be unreasonably impacted by the access.
- The information requested relates to anticipated legal proceedings.
- The information relates to negotiations with the individual requesting access.
- Giving access is unlawful.
- There is a legal order barring access.
- The access is (likely) related to an unlawful activity or serious misconduct.
- Giving access would hinder enforcement.
- Access would reveal commercially sensitive decision-making information.
You can read more about the grounds for refusal in the OAIC’s APP 12 Access to personal information guidance.
Charging for access?
You can’t charge people for making a request. However, organisations (not government agencies) can charge for giving access, provided the charge is not excessive (APP 12.8).
When considering how much you might charge, the OAIC advises that items that may be charged for include:
- staff costs in searching for, locating and retrieving the requested personal information, and deciding which personal information to provide to the individual;
- staff costs in reproducing and sending the personal information;
- costs of postage or materials involved in giving access; and
- costs associated with using an intermediary.
Charges that might not be considered reasonable include:
- a charge associated with obtaining legal or other advice in deciding how to respond to an individual’s request.
- a charge for consulting with the individual about how access is to be given.
Be careful not to use fees to discourage access requests.
The OAIC suggests that organisations should advise people in advance if there will be a charge for access and what it is likely to be. Organisations should interact with people requesting access to discuss options for minimising the charge, perhaps by limiting the request or changing the format for delivery. In any case, any charge that is imposed should be clearly communicated and explained before access is given.
More here Chapter 12: APP 12 Access to personal information | OAIC para 12.77 – 12.81.
Practical Tips for Responding to Access Requests
Here are some basic steps you may wish to implement at your organisation for responding to an access request:
- Verify the identity of the requestor. (Remember: sending personal information about an individual to someone else is a data breach. Verifying that the person is requesting information about themselves is very important.)
- Determine the nature and scope of the request.
- Calculate any charge that might be imposed.
- Collate the data (internally).
- Review the data to confirm it only relates to the individual requesting access to it and that it isn’t subject to any other grounds for refusal listed above.
- Write to the data subject to either state your grounds for refusal or confirm you have the data, along with details reminding them of their rights. If you plan to grant access to their data, advise the individual of any charges for access and confirm the format for delivery
- If necessary, liaise with individual on the extent of the request, format for delivery and relevant charges.
- Once agreed, you may issue an invoice.
- Once you receive payment, ship the data, or allow the requestor to view it.
Other Best Practices for Responding to Access Requests
These best practices can help your organisation fulfill its privacy obligations swiftly and simply:
- Make sure someone is accountable for access requests.
- Keep an accurate data inventory, so you know what data you collect and where it is stored.
- Help data subjects understand and effectively invoke their rights. For instance, instead of sending a refusal or very large invoice to a data subject (in hopes of deterring them), work with them to narrow the scope of the access request or the format for delivery.
- Document your steps when managing access requests.
- As always, collect data with purpose and ensure your organisation has implemented an appropriate data lifecycle (that includes destroying data when it is no longer needed).
Manage Your Organisational Data Better with Privacy 108
Our data management programs help organisations establish and grow their data management capabilities. This helps to ensure compliance with your privacy and security legal and regulatory obligations.
Our team will work with you to develop a tailored data management plan that contemplates your people, processes, and systems.
Reach out for a free consultation.